Create local login for Linux VMs: Difference between revisions
No edit summary |
No edit summary |
||
| Line 27: | Line 27: | ||
'''''NOTE: The users created with this code block will be able to SSH to your virtual machine (if port 22 is allowed) and have root access. Protect the password carefully! | '''''NOTE: The users created with this code block will be able to SSH to your virtual machine (if port 22 is allowed) and have root access. Protect the password carefully! | ||
[[File: | [[File:CloudConfig.png|border|600px]] | ||
Revision as of 17:08, 28 February 2025
This article will help you inject a local username and password into Linux instances at boot.
Some users prefer to use private keys to grant themselves access to their virtual machines, but some users prefer to simply define a username and password that will allow them to login directly to the console or easily over SSH. With most Linux based operating systems, the process to do this is easy.
Input a Cloud config
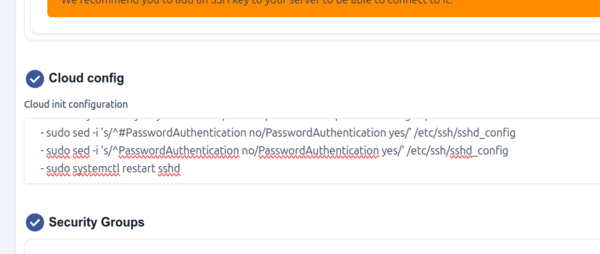
During instance creation, there is a menu called the 'Cloud config'. This is where special commands can be input that will be executed automatically during first boot. Here is an example of a block of commands that can be put into the Cloud config menu to create a local username and password.
#cloud-config
users:
- name: myadmin
groups: sudo
sudo: ['ALL=(ALL) NOPASSWD:ALL']
shell: /bin/bash
lock_passwd: false
ssh-authorized-keys: [] # Ensure no SSH keys are required
ssh_pwauth: true # Enable password authentication
runcmd:
- echo "myadmin:MyEasyPassword1" | sudo chpasswd # Set password using chpasswd
- sudo sed -i 's/^#PasswordAuthentication no/PasswordAuthentication yes/' /etc/ssh/sshd_config
- sudo sed -i 's/^PasswordAuthentication no/PasswordAuthentication yes/' /etc/ssh/sshd_config
- sudo systemctl restart sshd
NOTE: The users created with this code block will be able to SSH to your virtual machine (if port 22 is allowed) and have root access. Protect the password carefully!