Create or edit a security group (Advanced Console)
This article will help you create or edit network security groups.
Security groups are like firewall rules that can be assigned to one or several network interfaces. A security group contains a list of allowed network ports, and any port not listed in the security group will be denied by default. Every network interface/port in must be assigned at least one security group, unless port security is intentionally disabled on that port.
Every project contains a 'default' security group. This group is set to allow all IPv4 and IPv6 traffic in the outbound (egress) direction, but denies all IPv4 and IPv6 traffic in the inbound direction. If you set up your first VM and find you can't ping it, this may very well be why! Following the steps below will allow you to create a new security group for your VM (or edit an existing security group).
Create and edit a security group
Login to the DataTenant Cloud. Navigate to the Project, Network, Security Groups menu.
To edit an existing security group, choose 'Manage Rules' for the group you want to edit. Otherwise, to create a new security group, choose 'Create Security Group' and give your new security group a unique name.
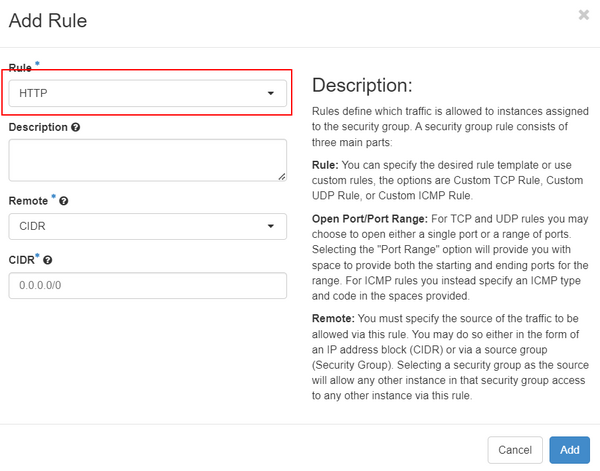
In the 'Manage Security Group Rules' window, you can add or delete any rules you would like to control the flow of network traffic to/from your network interfaces. For example, a generic 'Web Server' security group might need to allow inbound HTTP and HTTPS traffic. To do this, click 'Add Rule' and select 'HTTP' from 'Rule' dropdown.
In the 'CIDR' field, you can choose to only allow this new rule to be valid when coming from a certain IP address or range. For example, a user could choose to only allow HTTP traffic if the source IP address is in the '192.168.0.0/24' network. Leaving the default '0.0.0.0/0' in the 'CIDR' field will allow traffic from any IP address.
Click 'Add' to save the rule.
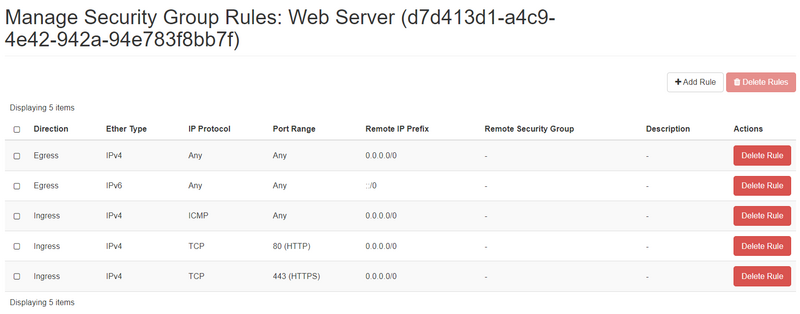
A fully completed ruleset for a public web server might look something like this:
In this example, the VM using this security group would be able to send all types of traffic inbound, and would allow inbound HTTP, HTTPS, and ICMP traffic from any source. All other inbound traffic would be denied.
For more information about how to change security groups on existing VMs, please review the Changing security groups article.